Phishing Email Summary
NOTE: THIS SCAM POSES A HIGH RISK BECAUSE IT ATTEMPTS TO STEAL BOTH AUTHENTICATION INFORMATION AND DUO CODES.
Description of Phishing Scam:
This phish attempts to steal login credentials and Duo login codes by redirecting recipients to a fake login page. The phish and login page steal U-M branding and use forged U-M email addresses to appear more realistic.
The first part of this phish is an email claiming that your Duo token is "out of sync." The email uses forged U-M addresses for the Team Dynamix system. This gives the appearance of the email having originated with a known U-M ticketing/Help Desk system familiar to many recipients. The reply-to address is also set to Team Dynamix. Links in the email may appear to be to weblogin, but they are also fakes.
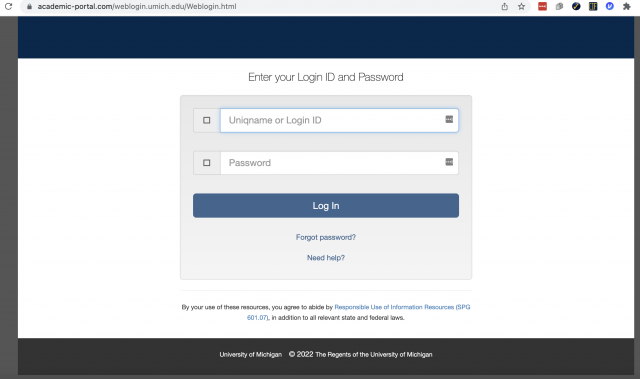
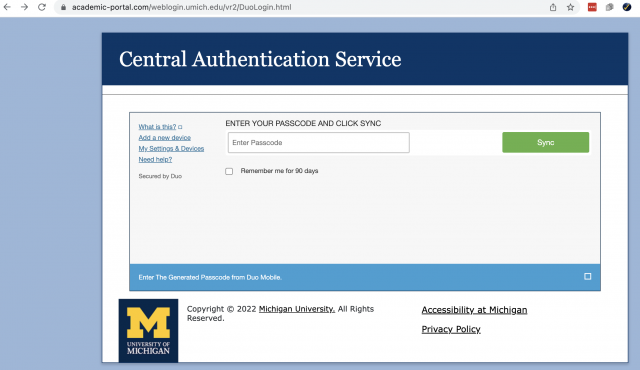
The second part of the phish is a fake weblogin page that also steals U-M branding and asks users to enter credentials and to also supply Duo codes. A first attempt to enter credentials may result in an error and redirection to a second phishing page that claims to be the "central authentication" page. This asks the user to put in a Duo code.
How to protect yourself:
Because branding can be copied and stolen and email addresses faked, diligently checking the URL of a login page is the best way to avoid this and many scams. Text in the link may say weblogin.umich.edu, BUT the URL of the page it takes you to does not match. In the screen shots below, you can see that the email uses "weblogin" as text with a hyperlink pointing to a fake address starting with "academic portal."
When logging in, always check that the URL on the page you arrive at says "weblogin.umich.edu" with nothing before it. Note that if you have already authenticated to weblogin, going to that address should send you to Wolverine Access.
What to do if caught by this scam: Anyone who thinks they may have been a victim of this scam should immediately change their password and unenroll then re-enroll with Duo.
Phishing Email Text
U-M Weblogin
DUO AUTHENTICATION
This is to inform you that the school database was currently upgraded and your Duo token got out of sync. Follow the steps below to sync your Duo two-factor authentication to the school database.
Step 1: Open the Duo Mobile app, In the Duo Mobile app goto michigan university and tap the key icon on the right side of the screen. A six-digit passcode will display, copy the passcode and proceed to step 2.
Step 2: Click the link below to Goto the school portal and enter the passcode to sync to the database.
[Link removed for safety - note that this link may use the text "weblogin.umich.edu" but that if you hover over the link you can see that it points to a fake login site, NOT the real weblogin!]
Failure to do this will result into error when trying to login the school website over time.
This page displays best when JavaScript is enabled in your web browser. JavaScript is required for two-factor authentication.
By your use of these resources, you agree to abide by Responsible Use of Information Resources (SPG 601.07), in addition to all relevant state and federal laws.
University of Michigan
© 2022 The Regents of the University of Michigan
======
Entering a password gets you an "error" prompting to enter password again. Upon second entry, you get forwarded to a fake "central authentication" page, asking for a duo passcode. As per "step one" in the phishing email. Duo passcodes can be used once and are valid for 30 days.